Step 1
Get Target
You first have to know your target to perform the PAM degration attack. We will connect to our system. We will use password 1234.
~ $ passwd
~ $ sshd
~ $ ssh unknowm@localhost
Step 2
Script Automation
It wouldn't be that easy to start to run manual commands like find / -perm /4000 2>/dev/null. That will be a total waste of time. Instead there's an automated script called PEASS-NG. Thai is a tool built by carlospolop and it is an automated script that helps in privilege escalation by find out files like misconfiguration, writable files, exposed password and so more:
~ $ unknown@kali : # git clone https://github.com/carlospolop/PEASS-ng
Step 3
Time for Attack
Now we have to know what we want to get and have the look for a misconfiguration. Now what we are trying to do is that, there is a directory called pamala that can only be access by root that has the password of the computer. But since we don't know the root password so we can't view the file in the pamala folder. To bypass this, we will move a directory where the pam instructions are kepts. These are modules kept for what to do when a user ttys to view a restricted directory, change to root, etc.
~ $ unknown@kali: # cd /usr/lib/x86-64-lib/security
You must be wondering how we got this information of the directory. We use the PEASS-NG tool and it told us that user(which is us) has the permission to write and delete any pam file in the security folder. To run PEASS-NG in Linux go to it's directory PEASS-ng/linPEAS/builder and make file linpeas_base.sh executable by typing chmod +x linpeas_base.sh. Then execute it by typing ./linpeas_base.sh
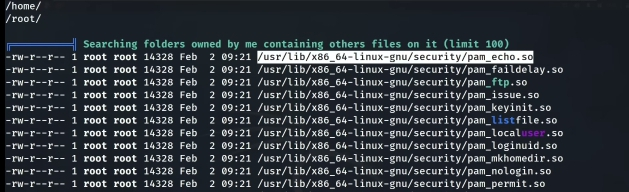
PAM degration
In thea love image, you will notice that the security folder is owned by the user. This is the PAM degration. The developer of Linux did not configure the permission properly so it makes it open. Also, you will see different .so files. And you will see a pam_permit.so file and a pam_deny.so file. What you will do is to delete the pam_deny.so file(because we have permission to do so) and copy the pam_permit.so file to pam_deny.so . Now here's what happened:
- When we delete the pam_deny.so and copy pam_permit.so back into it. It does the same action.
- So even when we get the password wrong it will still give us root access because what it will do permitted users, it will also do to restricted users. How cool is that.
Now we switch to superuser
:
user@kali:~$ sudo su
Password:
Now, you can do any thing on the system. From changing of p
password, removal of users to even use of password. I hope you enjoyed this tutorial, see you next time.



